Since so many blogs, including many that regular visitors to TPV have, use WordPress, PG thought the following might be helpful.
From Wordfence:
90 Billion Malicious WordPress Login Attempts
Over the course of 2020, Wordfence blocked more than 90 billion malicious login attempts from over 57 million unique IP addresses, at a rate of 2,800 attacks per second targeting WordPress.
Malicious login attempts were by far the most common attack vector targeting WordPress sites. These attempts included credential stuffing attacks using lists of stolen credentials, dictionary attacks, and traditional brute-force attacks.
Key Takeaway: Use Multi-Factor Authentication to Protect WordPress
While the vast majority of malicious login attempts targeting WordPress are destined to be unsuccessful, it only takes a single successful login to compromise a WordPress site. The brute-force mitigation provided by Wordfence is very effective, and using multi-factor authentication adds another layer of protection to WordPress logins.
Multi-factor authentication can completely prevent attackers from gaining access to a site via automated login attempts. This holds true even in unfortunate cases where user accounts on a WordPress site are reusing credentials that have been exposed in a data breach and haven’t yet been updated.
. . . .
4.3 Billion Vulnerability Exploit Attempts Targeting WordPress
Wordfence blocked 4.3 billion attempts to exploit vulnerabilities from over 9.7 million unique IP addresses in 2020. Here were the five most common attacks over the course of the year:
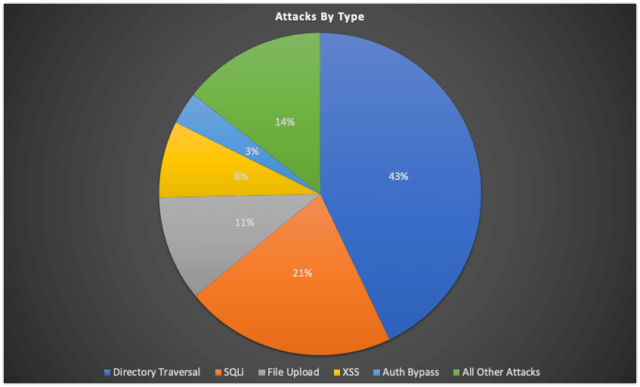
- Directory Traversal attacks, including relative and absolute paths, made up 43% of all vulnerability exploit attempts, at 1.8 billion attacks. While the majority of these were attempts to gain access to sensitive data contained in site wp-config.php files, many were also attempts at local file inclusion (LFI).
- SQL Injection was the second most commonly attacked category of vulnerabilities at 21% of all attempts with 909.4 million attacks.
- Malicious file uploads intended to achieve Remote Code Execution(RCE) were the third most commonly attacked category of vulnerabilities at 11% of all attempts with 454.8 million attacks.
- Cross-Site Scripting(XSS) was the fourth most commonly attacked category of vulnerabilities at 8% of all attempts with 330 million attacks.
- Authentication Bypass vulnerabilities were the fifth most commonly attacked category of flaws at 3% of all attempts with 140.8 million attacks.
. . . .
Malware From Nulled Plugins and Themes Is the Most Widespread Threat to WordPress Security
The Wordfence scanner detected more than 70 million malicious files on 1.2 million WordPress sites in the past year. The vast majority of these sites were cleaned by the end of the year. Only 132,000 sites infected at the beginning of 2020 were still infected by the end of the year, many of them likely abandoned.
The WP-VCD malware was the single most common malware threat to WordPress, counting for 154,928 or 13% of all infected sites in 2020. Overall, the Wordfence scanner found malware originating from a nulled plugin or theme on 206,000 sites, accounting for over 17% of all infected sites. Other obfuscated PHP backdoors made up the remainder of the top 5 most widely detected threats.
Link to the rest at Wordfence
PG says that you’ll spend far more money (or time) either trying to get your site back online or hiring someone to do it for you than any money you pay for malware protection. Also, while your site is down, nobody is able to learn more about you and your books.
Whenever PG reads the standard warnings about removing unused themes and plugins, he always double-checks TPV for any of those. It takes about 15 seconds.
One additional suggestion he’ll make is to update your theme promptly if you see the creator of the theme has an upgrade available. Sometimes updates are released, at least in part, to toughen up the protection of the site or to remove a potential vulnerability in a theme or plugin.
PG has used Wordfence for several years and has had no problems with anybody getting through. Typically, TPV is hit hundreds of thousands of times per month with malware attacks and none has ever gotten through.
There are other very competent malware protection software/service add-ons. Here’s a link to one of many articles you can find online reviewing various security products.
If you don’t use WordPress, it’s easy to find malware protection for other blogging software/platforms.
I also recommend adding custom author slugs and defaulting to something that does not match the username. A password like username is much less likely to be bruteforced than something guessable or available on the site.